U2F Update – including mobile, passwordless, and more…
U2F Update
Wednesday3C
Convener: John, Jerrod, Stina
Notes-taker(s): John Fontana
Tags for the session - technology discussed/ideas considered:
Discussion notes, key understandings, outstanding questions, observations, and, if appropriate to this discussion: action items, next steps:
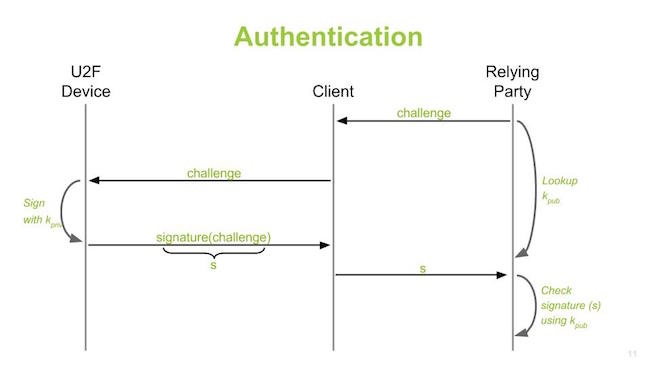
It is public key crypto
Benefits over the OTP, prove this is a real person.
don’t need third-party service.
I can log in to bank, gov. school. No secret is shared.
New set of encryption secretes when you login.
Can allow high scale, high privacy security.
There is no one controlling the global scale of identity.
Code is open and free.
Works with Chrome’ we’re working with Mozilla for them to adopt U2F Building ecosystem with many authenticators. Will be choices for all sorts of servers, services, biometrics, authenticators, There is a registration process and authentication process You can have many challenges in each session, not just initial login The FIDO stack can be built into any software, it is now prominent in browsers, Chrome, Mozilla working on it. What about mobile.
Mobile is about apps, a mobile app could do software key gen, and that app will basically be your fido client and your authenticator.
The future state is that the platform will provide the plumbing,
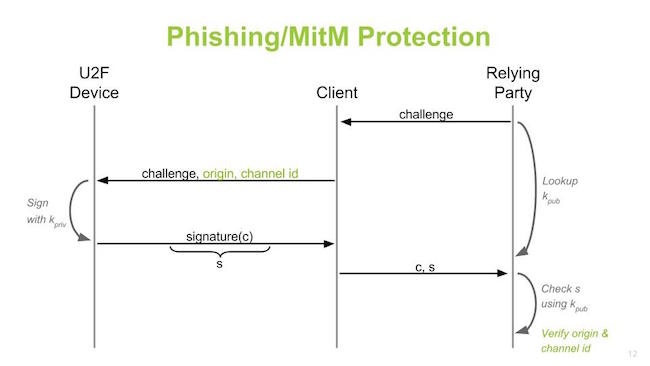
Apple is not on board at all now. Their support would be app level support and not device level support. Phishing and man in middle in the protection.
Origin is important , the client can verify where the response comes from. It fights re-direction.
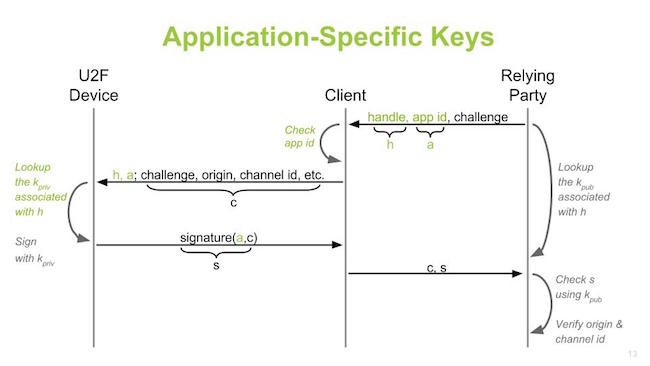
Application specific keys layer on top.
OTP notion today is symmetric. If every server does symmetric, you will have a mountain of codes. Independent of passwords look at strong two–factor today.
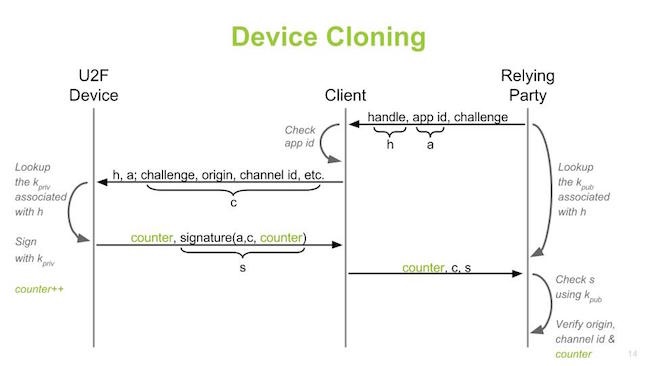
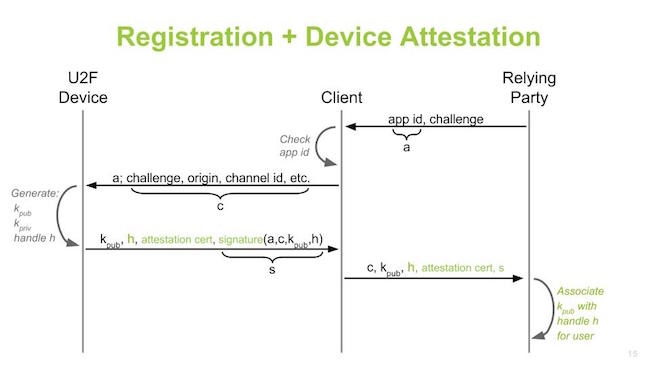
Device cloning – protection against this. Registration and device attestation.
Need to have bit to store public key and verify this is device you want to work with
So in the protocol we have attestation, relying party can decide which authenticators to trust.
Maybe this authenticator has secure element, transports over USB, I make assumptions what this authenticator can do …
You can trust vendors that produce the device, registration , once you have bound keys, can do bootstrap sessions on new devices.
Registration is critical, you can go bootstrap other things. You bootstrap a secure account to device and you can use it everywhere. Adding u2f support
Clients are there.
Critical thing for U2F public keys for those devices. Q: How do you validate a hardware device?
FIDO has certified devices, that is one area. You can check signatures.
As ecosystem grows. We see platform support as key. U2F final specs are one year out, industry leadership is needed for evolution.
We know public Key crypto works, the industry failed at first with too much infrastructure. Now that is gone with this. And we need to get it baked into platforms
PROTOCOL DESIGN