Principles of User Sovereignty (1/3)
Principles of User Sovereignty
Session: 9C
Convener: David Husseby
Notes-taker(s): Grace
Tags for the session - technology discussed/ideas considered:
Discussion notes, key understandings, outstanding questions, observations, and, if appropriate to this discussion: action items, next steps:
David Husseby
Where we are now:
- FB/ Google: Use the system and adhere to the rules, this is one extreme of the system.
- Surveillance capitalism, set up such that people are rewarded enough to not revolt.
- At urging of Sam Smith, DH started to wonder: what is the other end of the spectrum.
Link to session slide deck presentation, provided by Dave Huseby:
http://docs.google.com/presentation/d/1V1t6m217EFN8xOw5Zb6Mwr3LBp96O5JFID543io_XME/edit?usp=sharing
Chat Thread:
From Adrian Doerk to Everyone: 05:52 PM What is surveillance capitalism? A video by me: http://www.youtube.com/watch?v=t_aNHKait1o
History, David
- User sovereignty as a term has been use since 2011, first person public speaking was Mitchell Baker, head of Mozilla.
- Similar ideas, Declaration of Independence of Cyberspace used similar terminology. Our jurisdiction is different.
- In 1996, Technologists like ourselves were asserting user sovereignty and were worried about government incursion.
- In 2011, MB statement is about violation of user privacy. It went from government to corporation as the concern.
- In 2020 it’s around the hand-in-glove cooperation between corporation and government, so you can see FB saying that they will disallow anti-lockdown organization posts. FUrthering the power of corporation and governments
From Heather Vescent to Everyone: 05:57 PM Question: Which government are you referring to? US gov or foreign Govs (who do information operations)?
- DH: It could be anybody who’s job is to direct policy.
- Timothy Ruff: It could be any entity that could jail you or coerce you with guns
- It could be your own government
J Searles: The Utopia of Rules, Dave Gravers
Heather: Had my own thoughts about how the role of government has shifted dramatically in last 3 months based on my research on espionage. I had no idea of this prior to my research. One of hte most radical ideas I came up with was, I learned I support government surveillance more than corporate surveillance. The governments have the guns but the corporate surveillance doesn’t have responsibility.
Chris: I would agree. There is no sense of principles that dictates
Doc Searles: Depends on what government you are talking about. Reason we are less disturbe about private kind is because they just wnat to spy on us to sell us shit, but there is a lot they could do that we aren’t aware of
Heather: Info gathered by private sectors has been used by foreign governments. You could argue that FB and Twitter are weapons used against various countries.
Chris Buchanan: In US under supreme court rulings, Data collected by private companies that the government can buy is not considered surveillance and not subject to the same rules as government laws. So you’re giving it to the government without any oversight.
Heather: That was the problem with PRISM, because governments found a way to get the data without abiding by the laws
Jeff: Governments are ideally formulated by their communities. Business can aggregate that information in a space where they operate on their own and use force. There is a lot going on that it government agnostic. Deep tech is scary Aaaaaand… going back on track as the slide set begins to operate.
Principles of sovereignty (Slide 1)
5AM is the project David is working on, offering a new term of decentralization. People use distributed and decentralized interchangeably although people will say that decentralization is about power and rights. I’m suggesting that decentralization is the direction in which user sovereignty increases.
From Phil Windley to Everyone: 06:08 PM Sam is the mascot for full user sovereignty http://www.windley.com/archives/2015/01/re-imagining_decentralized_and_distributed.shtml
The Six Principles
This is for the most extreme end of the system.
- Absolute privacy by default. System knows absolutely nothing about the user. For example, a blind relayer might not need to know anything.
- Absolute anonymity and zero correlation by default (TOR level IP masking). Privacy to maintain leverage over a system that seeks to monetize their interactions. Primary tool against using data against someone is anonymity. Full control over what they share with other users.
- What, not who. Principle about designing authorization of system to be around what you are and what you can prove about yourself. Skipping identification and going straight to authorization. Identification today we use as the means to authorization and that is not necessarily a requirement. Would it be possible to build a payment system where content creators could collect fees from content viewers in a system which knows nothing either about the identity of the creator of the subscribers. If you look at the AML and KYC systems, these are all about law enforcement.. The biggest hurdle is biggest payments systems ban this. In theory, it is technologically possible. Someone could show they are a legitimate company with ability to collect money, and subscribers could provide KYC authorization without identity information.
Next 3 are the ones we usually discuss here.
- All data and operation are governed by open and standard protocols and formats. Today IMAP for email follows this. This works because there is a standard data protocol and format. This gives a tool to verify full user sovereign systems. This is how certification is done at the Linux foundation.
- Strong encryption by default to enforce data control. This is about the user knowing who is using what, where data is and the ability to delete.
- Informed consent. Any time we violate any of the other principles for legal or regulatory reasons, the system must get informed consent of the users, with the understanding that anyone can withdraw consent. Timothy says any decision making, and David says we don’t know why AI makes decisions. Any balanced terms of use between user and system.
CHAT:
From dsearls to Everyone: 06:15 PM open standard protocols and formats assure not only portability but what economists call *substitutability*. this is also what Dave is talking about here.
From Timothy Ruff to Everyone: 06:16 PM Doc, chime in please
From dsearls to Everyone: 06:16 PM Phil wrote about this in 2014, here: http://www.windley.com/archives/2014/03/substitutability_is_an_indispensable_property_for_the_internet_of_things.shtml
From Timothy Ruff to Everyone: 06:16 PM Doc, we learned a lot of this from you, we'd be honored to have you chime in I realize this is standing on the shoulders of giants.
Timothy Ruff: Doc sees that there’s a lot of top-down versus bottom up. What’s the benefit for individuals. If you do not simultaneously address what are the rights of the organizations, and why would they change all their systems, then it’s not going to go anywhere. We need to have balance here. Not say this is a user revolt. We want a balance of power. We want more than we have so each one of these principles about what is the benefit for the organizations.
From KathrynHarrison to Everyone: 06:17 PM What % of the general population would actively advocate/ ask for these principles? I agree with them but think it’s a small audience today.
From dsearls to Everyone: 06:18 PM I'm more wide than tall. Like a turtle. :-)
From David Huseby to Everyone: 06:18 PM +1 Doc
From KathrynHarrison to Everyone: 06:18 PM Also question is incentives
From David Huseby to Everyone: 06:18 PM right
I have a little on that too
From KathrynHarrison to Everyone: 06:18 PM Free data and information has been crack for the General population for the last 20 years
From David Huseby to Everyone: 06:18 PM PII is toxic waste
From JeffO-StL to Everyone: 06:19 PM Re-evolution, not Revolt
From JeffO-StL to Everyone: 06:19 PM Revolution
From Kaitlin Asrow to Everyone: 06:19 PM data pollution
From Me to Everyone: 06:19 PM What's wrong with a user revolt? Organizations are not living beings. They are created by us.
From Gabe Cohen to Everyone: 06:19 PM Substitutability = easier to bring new users to your platform
From dsearls to Everyone: 06:19 PM Relevant: http://www.gapingvoidart.com/gallery/dinosaur/
From johnnyfromcanada to Everyone: 06:19 PM We are anchoring the negotiation with society!
From JeffO-StL to Everyone: 06:20 PM fat fingered last) Re-Evolution (of systems and values) is evolved Revolution maybe...
From Marc Davis to Everyone: 06:21 PM “Informed consent” is highly problematic in practice. Most TOS and Privacy Policies are “contracts of adhesion” (asymmetric power enforced without any alternative choice). What I see missing here is a clear articulation of what rights each party actually has or should have. If you want true user sovereignty, the rights and legal and regulatory frameworks need to be clear in empowering the self-sovereign person. I can point you to my talks on Digital Feudalism and Digital Enlightenment from 2010 on.
Doc: We assume that we are the ones consenting to their terms, but it should be able to go both ways. We wouldn’t be talking about this at all if a simple request of do not track in a browser had been obeyed 10 years ago, but it wasn't’.
David: In that world we could negotiate our own terms. In my next talk about fundamental problems of distributed systems, if you don’t adhere to these 6 principles, you subject the system to corporate capture. It opens the door for a company to provide a centralized solution.
From Marc Davis to Everyone: 06:21 PM “Informed consent” is highly problematic in practice. Most TOS and Privacy Policies are “contracts of adhesion” (asymmetric power enforced without any alternative choice). What I see missing here is a clear articulation of what rights each party actually has or should have. If you want true user sovereignty, the rights and legal and regulatory frameworks need to be clear in empowering the self-sovereign person. I can point you to my talks on Digital Feudalism and Digital Enlightenment from 2010 on.
From David Huseby to Everyone: 06:21 PM right
From Timothy Ruff to Everyone: 06:21 PM Grace: user revolt has the same problem as what we saw on Thor: Ragnarok: if you plan a revolution, you'd better pass out enough fliers! Seriously, it's hard to get enough users to care enough to execute a successful revolt. In the end it's best to do it together, with the best interests of orgs considered, too.
From Dennis Landi to Everyone: 06:22 PM Got it. thanks
From Chris Buchanan to Everyone: 06:22 PM Doc, one of the interesting things about having bilateral privacy policy is the potential to match users with services.
From Benedikt Olek to Everyone: 06:22 PM I think user sovereignty comes also with a lot of responsibilities. In SSI, you might need to properly handle your secrets (priv. Key). If somebody gives you a perfect anonymity tool (like SuperTor), you still can accidentally doxx yourself and so on
From Me to Everyone: 06:23 PM The new CAL Open Source license is relevant to this talk. I can elaborate. http://medium.com/holochain/understanding-the-cryptographic-autonomy-license-172ac920966d
David: Preview of problems in distributed systems (missed the main points), but because the problems of distributed systems caused GitHub to be bought by microsoft and they have 30% of the Opensource project and host the top 100 opensourece projects. And evne the projects that DLF hosts are still on Github. The communities should use the best tool but there are people who are nervous about Microsoft owning Github. We are seeing streamlining of Github with AZP and now were’ seeing Windowssubsystems by Linux. They’re looking out for their business. By not providing fully decentralized systems, Git opened itself up to capture. I’ll go into that deeper in the next session.
From dsearls to Everyone: 06:24 PM Agree, Chris. The question is how that gets framed up. If it's always up to the service, you have as many policies as there are services.
From KathrynHarrison to Everyone: 06:27 PM Means quality of decentralized service has to be 10x traditional systems if it is going to get adoption. Most people are pragmatic.
From dsearls to Everyone: 06:27 PM We're up to 77 people here. Might be a record for a breakout. 78
From johnnyfromcanada to Everyone: 06:27 PM In Timothy’s state-of-the-art session yesterday, we raised the notion of “SSI Certification” and/or “SSI Declaration” that companies should align and commit to. Seems to me that these principles (or similar) could be a foundation for such. Also such a certification would need to be tiered / levels (CMM), just as these 6 principles are likely unattainable fully (aside from some exceptions).
From Timothy Ruff to Everyone: 06:28 PM True. SSI took the time to verify doctors in the UK from half a day to a few seconds. That's easily 10X.
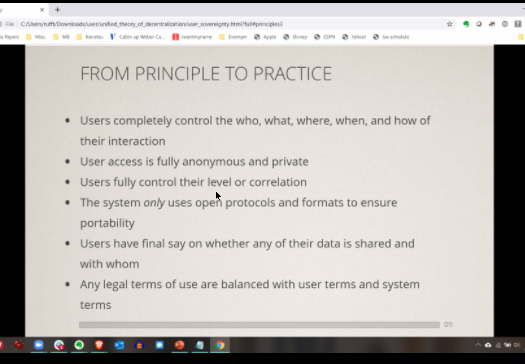
From Principle to Practice. What would it look like
- User would have full control
- User is fully anonymous and private by default
Joyce told me this story, I go to this coffee shop every day, and I have for years, and they offer 20% off for first time customers. what about me? I’ve been keeping you in business for years! The reality is like this, a lot of systems work like that. But we could show up as first time customers every time.
Joyce: to add to that, what would happen if as soon as we walk into a mall, every shop knew we were looking for a pair of black shorts. What negotiating power would we have? We could not possibly get the best deal if they all knew that. We want our ability to hide that information about ourselves to be built into the system.
DAvid: By anonymous it means I am not radiating any information that you can gather that would allow you to correlate me across time and space.
Doc: If we are outside our regular social circles, we are nameless. A nonymous, not nameful. We should have that as a default online and then add in nonomous, or credential as required or as we choose.
From Me to Everyone: 06:30 PM You're obviously going to the wrong café. My health food shop gave me a discount after I'd been coming for 3 months.
From Wendell Baker to Everyone: 06:30 PM What about that bar where everyone knows your name?
From Cam Geer to Everyone: 06:30 PM Dave that is the first state - we are looking at — window shopping
From Wendell Baker to Everyone: 06:30 PM just trollin ya :-)
From David Huseby to Everyone: 06:30 PM yup
From Kaitlin Asrow to Everyone: 06:31 PM whoever holds more information is able to capture more surplus from the transaction
From dsearls to Everyone: 06:31 PM Dave's talking about what our natural state of anonymity is in the physical world, as a default outside the circles where we are known.
From Jeffrey Aresty to Everyone: 06:31 PM IBO feels the need for a Declaration of Rights which establishes a framework for adoption - we would appreciate your comments
From Timothy Ruff to Everyone: 06:31 PM The 10X requirement Kathryn's referring to comes from "The Change Factor," which posits that users require a 10X improvement before they'll overcome the switching costs of making a change. There's a whole book and other stuff about it.
From Jon Lewis to Everyone: 06:31 PM I think the analogy of the mall is flawed. If all of the merchants knew that we were looking for black shorts... we would ultimately get a getter deal. The merchants would compete for the business and our ability to leverage a competitive market would increase.
From KathrynHarrison to Everyone: 06:32 PM I think we need to look more to models for how we operate in analog world...
From Jon Lewis to Everyone: 06:32 PM We want them to know what we are looking for.
From Cam Geer to Everyone: 06:32 PM The person / user chooses whether to have a relationship with the business / service. Otherwise default state is anonamous
From Cam Geer to Everyone: 06:32 PM The person / user chooses whether to have a relationship with the business / service. Otherwise default state is anonamous +1 Kathryn — this is the primary discovery action of the Me2B Alliance
From dsearls to Everyone: 06:33 PM Right, Cam.
From Me to Everyone: 06:33 PM @dee, I am happy to discuss the CAL license here or set a session about that.
Chris: It takes a willful decision on the side of the platform to ignore that data.
From Jsearls to Everyone: 06:34 PM I’ve been saying this is “natural anonymity” I’m known as a person, but nothing more until I want to reveal more.
From George Fletcher to Everyone: 06:34 PM not named doesn’t mean not correlated. As humans we are global correlateable identifiers unless we go to extreme lengths
From dsearls to Everyone: 06:34 PM I think what Dave's talking about is each person as her own platform. Not about what service platforms (apple, google, et. al) are doing.
From johnnyfromcanada to Everyone: 06:34 PM This extreme is likely asymptotic in practice.
Phil: You are nameless but not anonymous. I have a sophisticated system -- I don’t lose track of you as you walk past me on the street
Jeffrey archer posted a document.
From Cam Geer to Everyone: 06:34 PM yes…that is what the Me2B Alliance certification is driving toward. It is just the assertion
From johnnyfromcanada to Everyone: 06:35 PM Forgetfulness is a key part of GDPR (and others).
From JeffO-StL to Everyone: 06:35 PM @PhilW: The Human as a sensor package is a great topic of discussion.! I did a session at IIW..
From Juan Caballero to Everyone: 06:36 PM Is this the things OSP made for HoloChain ? http://medium.com/h-o-l-o/why-we-need-a-new-open-source-license-c8faf8a8dadd
From Cam Geer to Everyone: 06:36 PM +1 Grace
From Kaliya Identity Woman to Everyone: 06:37 PM The ioFoundation is working on something like this a universal declaration of digital rights starting with - http://www.theiofoundation.org/
From Cam Geer to Everyone: 06:37 PM And open source is even moving into base silicon http://riscv.org/
From dsearls to Everyone: 06:37 PM Forgetfulness dates from Brandeis & Warren's treatise on privacy as "the right to be let alone." (let=left)
Marc Davis: A lot of work was done on digital feudalism versus digital enlightenment, I can point to that. Relative to that, the talk seems to assume a kind of techno-determinism, that alternative technology will push the stack in the right direction. When you talk about the balance of user terms and legal terms. To have user sovereignty requires not only technology but also law, and regulation, it has to include rights, legal, and regulatory frameworks. not just through technology. The point about informed consent goes right to that. Informed consent tends not to work in practice.
DAvid: These are just principles.
Doc: We already have laws that are screwing things up. GDPR assumes we are nothing more than data subject. In the absence of tech, state of California decided we are just consumers and our rights are nothing more than our ability to ask for our data back. If we firm up everything in terms of the laws, we get locked up in the tech. We could start tech first and then have the laws follow the norms.
David: I’m a crypt anarchist but I’m also willing to put on a suit and talk to people in power. But I am also willing to do this first. We should always be willing to have the conversation, but I think this is a foundation for where we should start principles wise and as we design new systems.
My last slide of my last talk is about why Web 1 and Web 2 are centralized and why most of what’s coming out of Web 3 will also be centralized.
I don’t think we should ask permission.
Jefferey: Laws are not going to come from sovereign states. The International legal system is broken. Anybody in civil society can make a bunch of statements about how it should be. We need to state our position. Nothing you are saying is illegal in any country.
Chris Buchanan: This is a community project and I would like to participate in something like that and my corporation would like to be part of that. My company is involved in that. It’s hard to draw the connections with current reality when talking about biometrics surveillance systems. We want to lay it out and say “This is the perfect”. Then we can ask what policies are in the way of the perfect, and what are the incentives for people to move and what is the overall global strategy in how to prioritize our own efforts in the SSI community to move this forward to move this forward in away tha tisn’t behemoth resistant in every area. My experience with government is that they are for some of this. Having explicit consent is huge and it would solve some of the problems with technical surveillance. I think there’s interest within places that you would normally think of adversarial. Getting together with the group of folks who can speak to what the perfect is, and bringing in some naysayers and people who would say, well that won’t work because. Let’s start refining that. That's how you reach strategy. This deserves a serious amount of brainpower. It is the most important thing. We didn’t have stoplights before we had cars.
From David Huseby to Everyone: 06:44 PM +1
From Timothy Ruff to Everyone: 06:44 PM We're out of time... :-/
From Line Kofoed to Everyone: 06:44 PM +1
From Me to Everyone: 06:44 PM How do we provide you feedback
From Juan Caballero to Everyone: 06:45 PM yeah where's this go
Chris! Doing God's work
From David Huseby to Everyone: 06:45 PM let's meet in a garden room later this afternoon to talk about where this goes
From JeffO-StL to Everyone: 06:45 PM I would like to be available for such an effort (WG) as well.
From dsearls to Everyone: 06:45 PM There are groups working on some of this: http://me2b.us, http://customercommons.org, http://projectvrm.org
From David Huseby to Everyone: 06:45 PM or that ^^^
From Juan Caballero to Everyone: 06:45 PM ^ yes
From Marc Davis to Everyone: 06:45 PM The question is not only what laws are on the books, but what rights and agreements we want various parties to have in a world based on “self sovereignty”—i.e., look to contract law—the agreements individuals and organizations make with each other and that articulate their respective “rights and duties”—this is different from transnational, federal, or state legislation, but much more about the agreements parties make with each other.
From johnnyfromcanada to Everyone: 06:46 PM These principles can also be another simple way to help people to understand SSI in general (after telling them about wallets. :-) )
From Timothy Ruff to Everyone: 06:46 PM Haha Johnny!
From Kaitlin Asrow to Everyone: 06:46 PM I am concerned that the volume of contracts necessary to deal with every digital interaction is not tenable
From johnnyfromcanada to Everyone: 06:47 PM In fact, everyone’s wallet should contain these on an e-laminated card.
From Kaitlin Asrow to Everyone: 06:47 PM individuals cannot negotiate contracts at scale
From Juan Caballero to Everyone: 06:47 PM ^ the three groups Dsearls mentioned all work on that as a substantial focus
From Heather Vescent to Everyone: 06:47 PM My concern is that there are not people in the room with power to make this a reality.
From Juan Caballero to Everyone: 06:48 PM @Johnnyfromcanada, here's my attempt at that: http://www.caballerojuan.com/blog/ssi/the-next-big-thing-is-you/
From Kaliya Identity Woman to Everyone: 06:48 PM Before you talk - breath, figure out what you want to say, say it and then stop…and wait
From dsearls to Everyone: 06:48 PM Hope folks saw Jeff Aresty's shared document earlier.
From Jsearls to Everyone: 06:48 PM @heather, this speaker is saying that his corp is speaking to govt
From Kaliya Identity Woman to Everyone: 06:48 PM don’t feel like you need to fill the space - we can’t see each other and don’t have the natural body language.
From Timothy Ruff to Everyone: 06:48 PM @Heather... not directly, but indirectly we can do a great deal. I have some ideas, and Chris is talking about what he/Mitre can do, and there's gonna be way more...
From Me to Everyone: 06:48 PM I would be interested in that working group too!
From Marc Davis to Everyone: 06:49 PM A key intervention is a small set of standardized contracts that reflect “self-sovereignty”—expressed in simple, brief, language that a non-lawyer can understand and actually consent to—to standardize and make more efficient and transparent the rights and duties each party has.
From johnnyfromcanada to Everyone: 06:49 PM
Many domains head this direction of core principles. E.g., software engineering developed a “kernel”. Agile now has an “essence” (heart).
From Cam Geer to Everyone: 06:49 PM @ Kaitlin — that’s why the agreement direction needs to be flipped. Put users in control with a “bill of rights” they control and the business / govt / services agree to abide by them or the person / user doesn’t use their offering
From Heather Vescent to Everyone: 06:49 PM Also I’m not sure how much of this future I actually want.
Goal of my project is to build a fully sovereign github and Jira replacement.
From Kaitlin Asrow to Everyone: 06:50 PM @Cam, agree 100%
From Timothy Ruff to Everyone: 06:50 PM To each her own! For me, I want greater user sovereignty, freedom to take my data and relationships from platform to platform as I choose.
From Me to Everyone: 06:50 PM A bunch of people are working on developing a Git replacement on Holochain, you should get in touch with them.
From dsearls to Everyone: 06:50 PM I think we need one invention that mothers a necessity for everything Dave's talking about here. These principles should guide the development, for example, of digital wallets of credentials. Once corporate and government entities share and respond to the use fo these credentials, we may have the first traction required to internet investors and support by foundations and well-off individuals. In the absence of that tech, we're where we've been.