Practical UMA – curl commands etc…
Practical UMA
Wednesday 2J Convener: Josh Gubler
Notes-taker(s): Eve Maler and Scott Fehrman
Tags for the session - technology discussed/ideas considered:
Discussion notes, key understandings, outstanding questions, observations, and, if appropriate to this discussion: action items, next steps:
The UMA Work Group developed V1.0 and V1.0.1 of, and is further developing, the UMA protocol. See:
- http://kantarainitiative.org/confluence/display/uma/Home (where you can find a Join link and information about the IPR policy of the group)
The UMA Developer Resources Work Group is developing open-source client libraries, sample applications, and other resources to "seed the ecosystem". There is already work done on a Java "resource server client" (that is, a resource server as a client of the authorization server). See:
- http://kantarainitiative.org/confluence/display/umadev/Home (where you can find a Join link and information about the IPR policy of the group)
- https://github.com/kantarainitiative/wg-umadev
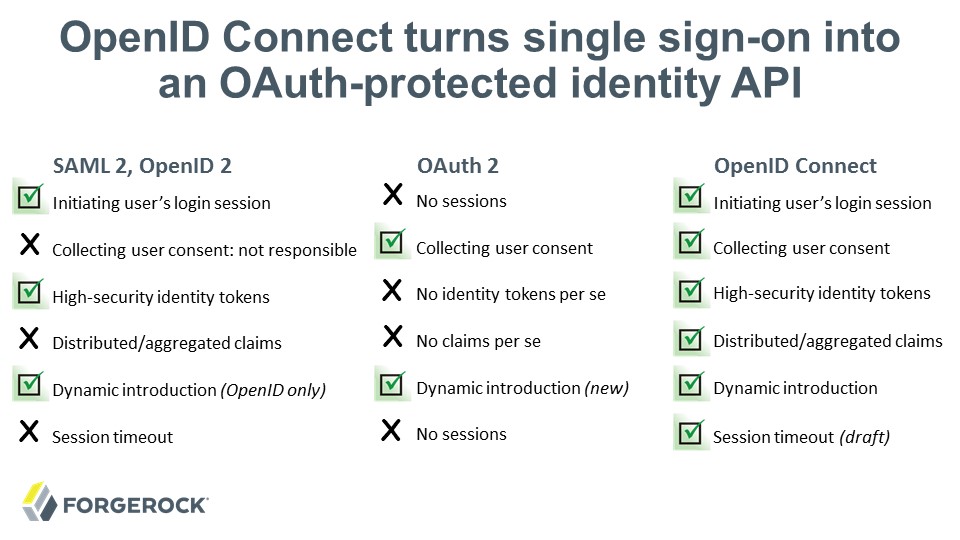
See the attached slide deck for a quick comparative description of OAuth, OpenID Connect, and UMA. Today, UMA can handle "narrow" and "medium" ecosystems pretty well, where the resource owner and the requesting party are in the same domain or in domains that have pre-established trust. The UMA WG is working on resolving architecture issues with "wide" ecosystems, where there is no pre-established trust between the relevant authorization server and claim issuer(s). The issue is kind of like a certificate authority problem.
See the attached "generic flow" PNG files for high-level and low-level versions of UMA messaging flows. Each request/response arrow has a reference out to the specific specification section. See:
- https://docs.kantarainitiative.org/uma/rec-uma-core-v1_0_1.html
- https://docs.kantarainitiative.org/uma/rec-oauth-resource-reg-v1_0_1.html
Q: What is OpenUMA? A: OpenUMA is the open-source project underlying Forgerock implementation of UMA in its ForgeRock Identity Platform. OpenUMA is based on the OpenAM and OpenIG projects, comprising the AS and RS components of UMA. See:
There are several other implementations of UMA, including open source. See: