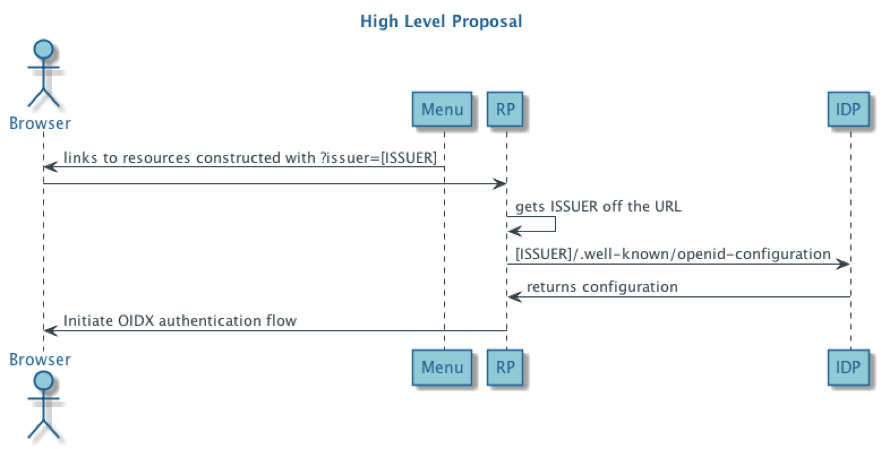
Open ID Connect hint on the URL – fight IP “authentication’ change EZproxy!
Open ID Connect
Tuesday 5G Convener: Judith Bush
Notes-taker(s): Judith Bush
Tags for the session - technology discussed/ideas considered:
Discovery, EZproxy
Discussion notes, key understandings, outstanding questions, observations, and, if appropriate to this discussion: action items, next steps:
<?xml version="1.0" encoding="UTF-8" standalone="no"?>
OpenID Connect uses WebFinger[RFC7033] to locate the OpenID Provider for an End-User. Once the OpenID Provider has been identified, the configuration information for that OP is retrieved from a well-known location as a JSON document, including its OAuth 2.0 endpoint locations. " Issuer discovery is OPTIONAL; if a Relying Party knows the OP's Issuer location through an out-of-band mechanism, it can skip this step and proceed to Section 4. issuer
REQUIRED. URL using the https scheme with no query or fragment component that the OP asserts as its Issuer Identifier. If Issuer discovery is supported (see Section 2), this value MUST be identical to the issuer value returned by WebFinger. This also MUST be identical to the iss Claim value in ID Tokens issued from this Issuer.
- Oauth flows don’t match the library flow model
- Will look into Google’s AMP protocol