Forget About Identity & Authentication (Discuss New Aproaches
Forget About Identity & Authentication (Discuss New Approaches)
Day/Session:Wednesday 3J
Convener:Andrew Hughes & Robert Mitwiki
Notes-taker(s): Alec Laws
Discussion notes, key understandings, outstanding questions, observations, and, if appropriate to this discussion: action items, next steps:
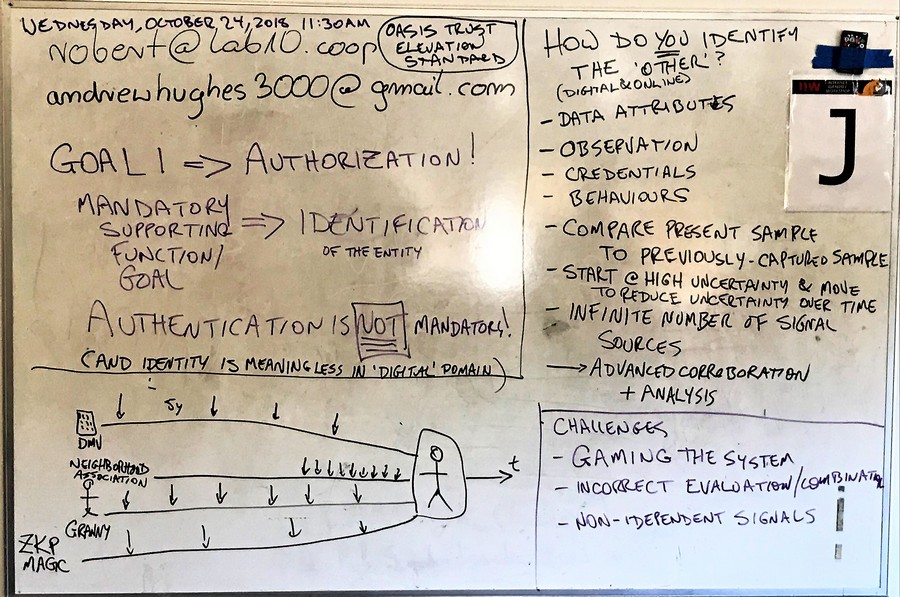
IDEA: identity is pointless in technical sense -> it doesn't exist
Identity does exist in the world, but we're not talking about identity
- talking about: authentication, credentials ...
- identity is label for collection of all of these services
in real world, no one know what 'identity' mean (as we discuss)
two things we actually do
1. authorization -> what a subject can do
2. identify the identity -> enough to look up authorization
method to identity someone, doesn't rely on any specific technique/technology
- proof of presence
Is there a way to track someone based on their patterns within an environment?
- use technology to measure
brings up identity vs identification
identity -> typically based on credential presentation
identification -> don’t actually need the credentials
to escape tracking in digital world
ex mobile device tracking patterns
- patterns stay the same even if you change devices
identification without attributes, based on patterns
crowd Q. is this surveillance-based identity
-> coopt targeted marketing as identification system
- observables
creating an identity through measurement
assumption that someone documents identity, put in a registry -> everything flows from there
another entity accepts the issued 'identity'
assume there is no such 'issued credential'
- we identify without paper/plastic credentials -> how to translate into a technical system
observed vs assigned attributes
observation to build attributes vs presentation of assigned attributes
cQ. local checking vs remote checking? different use case?
- lofty goal -> it's universal
- what is the nature of identification, how can we make this electronic
- is this device fingerprinting? this is identification
verification and proofing techniques, gathering evidence (sometimes from id docs)
- dyn and risk based authz services, and really identification services
idproofing: linking physical identity to a person
there is no common measurement framework to express id proofing and behavioral sensing’s are in the same domain
- allows supplementation of identity documents
- companies already do this to assess fraud
can we build this common framework to link behavioral and attribute-based identity?
Why is this the right direction? (shift from identity to identification)
- we have many different credentials -> can be lost/destroyed
- people would lose id docs
What is a good threat model for this? How can it be gamed? ie spoofing of location. Once people have motivation to attack... balance between effort and benefit
authentication is tied to 'time', in reality things are strongly ordered -> very hard to tamper
challenge w idproofing -> standard writing is b/w way. either identified or not. not really how it is. Is this continuous?
move from high -> low uncertainty
cQ. what we are calling identification would be called a risk score. identification to system vs many systems
supplement identity vs identification
cQ. for this to happen and connect risk scores, we need confidence in identity to relate to the behavior.
- start with a static proof of id and supplement with other techniques
cQ. how are scores made, and how can they be combined?
- standardization? error bars? number of sources, quality of data
what is the definition of a working system?
never a boolean, always a degree of confidence or assurance. probability based
risk model + threat analysis + other source to mitigate/change risk and make it measurable
acr shows what the 'person' did to authenticate
what can we standardize about these processes?
Take existing stuff and make into a patterns
key thing is time/timeline -> assume time always moves forward
registrar says 'I must identify you to issue a credential'
-> you show previous evidence with correlated data
-> shared events in the past, ie reregistration of license. vehicle permits
-> artifact memorializes the interaction
ie 'when you get murdered, make sure you sync your Fitbit' Fitbit tracks liveness, timelines didn't match and threw out an alibi
can we collapse the timelines between interactions with different entities?
score and assertion measurements mechanizes so that the can be compared
how to prove you climbed a mountain? take a photo? gps? you leave an artifact at the top, the next person can verify that it's there.
-> impractically of faking
-> the artifacts that you drop on the timeline show provenance of your 'identity'
website. I encounter website for first time, no access controls (anon access). they have identified you at protocol layer (at least). They don't care about authenticity of claim (ip addr), they never authenticate but they identify.
bank site. attempt to get $1. they both identify (username) and authenticate (with a proof)
how does this sync with privacy? access to data you need to perform this process
- private authentication assertions (zero knowledge proof) to address correlation
- ML model uncertainty vs proofs based on mathematics
- (non)independent data points -> especially when combining models
- secret algorithms 'black boxes'