Consent Management – Receipts Practices Standards
What Every Identity Professional Should Know: An Introduction to IDPro
Day/Session:Thursday 2G
Convener:Ken Klingenstein & Andrew Hughes
Notes-taker(s): Andrew Hughes
Discussion notes, key understandings, outstanding questions, observations, and, if appropriate to this discussion: action items, next steps:
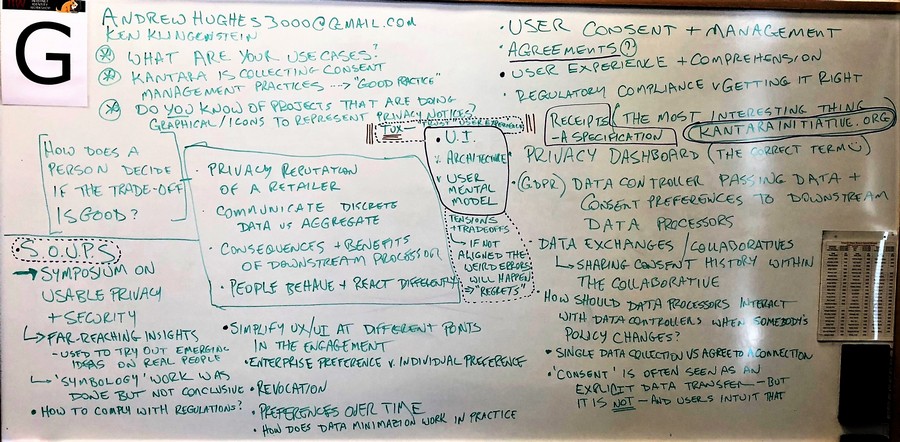
We discussed the topic of consent - use cases, receipts, definitions, issues to consider. Here are the whiteboard notes. The group decided on the most important topics and those are circled in purple.
(2) From Jeffrey Friedberg:
Thank you for letting me introduce the concept of the Trust User Experience (aka TUX) in your session.
When users are placed in the “hot-seat” to make a privacy, security, or trust decision, they are presented a TUX. It is made of 3 things: the UI that is shown, the underlying architecture, and the user’s mental model. When any of these three are not aligned, the user will likely make a mistake – one they usually will not realize until later when the outcome of their choice is explained to them. And at that point, they usually have regret (something that can be measured).
The TUX presented for consent is just one type of TUX. There are a number of different types of TUX including warnings (something bad could happen) and prods (a nudge to get you to do something). For consent the most common type is an “all or nothing” pattern. That said other patterns are possible, like a “haggle” TUX where the horse trade is negotiable.
Note, the T in TUX is for Trust not Trusted. The TUX is just that – something presented to the user related to a trust decision. Ideally the experience would be trustworthy (i.e. “trusted”), but we are unfortunately a long way off and many are deliberately deceptive or attempt to game the user into making a particular decision (per Cass Sunstein’s “nudge” theory). At the end of day, designers of TUX are really “choice architects” and ideally, they should have a responsibility to be fair. Testing the TUX in a system should become part of the threat model and the normal software development lifecycle. TUX best practices, as they become known, should be taught to developers and UX designers.
Per you request, attaching some additional background on TUX and some suggested best practices:
- A 2009 Blog introducing TUX concepts and a call to action. I posted the content inline at the end of this document in the appendix for convenience.
- Wallet card of TUX Best practices. I believe the email address is no longer being monitored.
- Video of a Microsoft Research presentation I did in 2010 on the End to End to Trust initiative that includes a deep dive on TUX. Link here. My session starts at 41:07 and covers the goals of the initiative (to create a safer more trusted internet), the methodology, and some innovative roadmaps of what needs to be built. At 1:06:26, seven key families of building blocks are summarized including improvements to digital identity, the use of minimum disclosure claims, rules-based access to data, and TUX (1:07:38) which is a horizontal and needed for just about everything. The deep dive on TUX follows (for 20 minutes) and covers both good and bad TUX and some interesting research take-aways. And at 1:26:04. why informed consent doesn’t work.
- Slide deck on End to End Trust from 2010. Link here. The deck covers similar content to the video above, but the slides are not compressed and useful as a companion to the video. The seven families of building blocks is posted on slide 23 and TUX is further explained with examples from slide 24 to 48.
Happy to engage others on TUX – the last two feet of end to end trust!
Jeffrey Friedberg
Appendix
Content below is from a blog I posted April 15, 2009
TUX: The Last Two Feet of End to End Trust
In his recent blog post, Scott Charney described a vision for End to End Trust. Core to the proposal is a trusted stack rooted in hardware. The “last two feet”, the place where the user interfaces with the system, requires special consideration. It’s where the user must make key trust decisions like: “Is this really my bank site? Should I install this software? Should I share my sensitive data?”
Unfortunately, the trust user experience (TUX) that is presented can be confusing to some users. For example, they may be perplexed by the written guidance or unfamiliar with the semantics of the security indicators. Many just click through these critical check points without fully understanding the implications.
How bad can it get?
Making a mistake here could expose the user to range of harms. At one extreme, installing rouge software could turn their system into a remotely controlled “bot” which can be used to send spam, enable identity theft, or worst-case help launch a cyber-terrorism attack. At the other extreme, choosing the wrong sharing model on social networking site could expose embarrassing photos to the wrong people, resulting in a damaged reputation and even job loss.
TUX vision and scope
Many consumers are uncomfortable having to make the trust decisions that are put in front of them. They would much rather just continue listening to music, buying products on the web, or chatting with friends. The trick is finding a way to increase their safety without distracting them from enjoying their digital lifestyle.
Poor TUX does not just affect consumers. It affects enterprises as well. It can lead to setting up the wrong configuration by an administrator. We have all seen the headlines: “Millions of records lost.” The other issue businesses face is connecting with their customers. Users are told to be very suspicious of email and to not click on links. This forces some business to create walled gardens on the web just to have a conversation. The vision for businesses is to help them better connect with their customers and to honor the trust promises they made.
Whenever possible, it is best to address trust in the architecture to avoid needing to ask the user in the first place. No TUX is good TUX. However, when the user needs to get involved, the goal is “trust at a glance.” It’s unrealistic to think users will manually inspect a certificate or read every line of a privacy statement. We must find ways to increase the user’s confidence they are making a good trust decision while reducing their need for doing all the leg work.
More than just UI
TUX is much more than just the user interface (UI) that is presented. It includes the underlying architecture of the system and the mental model the user has in their head. When designing and evaluating a TUX, all three elements need to be considered. Improving the UI will only take you so far. In some cases, changes to the underlying architecture will need to be made. Likewise, it is important to assess whether the user is likely to form the appropriate mental model for the task and take steps to create better alignment.
Creating great TUX is hard
Users come in with different goals, expectations, and experience. There may also be cultural differences. When it comes to creating great TUX, “one size” unfortunately does not fit all. We need to understand what will really help a user when they are in the hot seat. In some cases, providing clearer guidance may help. In other cases, it’s a design issue and new less complex controls need to be provided.
Some users would rather not deal with the risk analysis and would like to simply “call a friend” or “poll the audience”. As in the real world, consulting outside advice from people, communities, and tools you trust can play a significant role in making better trust decisions (and can reduce anxiety). The ability to conveniently tap this information is often missing in the TUX that is presented. Establishing a common framework for providing reputation feeds could help users connect with advisors they trust.
One additional challenge to highlight is habituation. For various reasons, many users have given up trying to fully understand the risks and have gotten in the habit of just clicking “Next, Next, Next” (when was the last time you read an end user license agreement?). It’s important to find ways to catch the user’s attention and guide their behavior to safer outcome when it’s really needed.
\
The path to better TUX
TUX is nascent discipline that draws from multiple domains (e.g., security, privacy, usability, accessibility, psychology, and anthropology to name a few). Across the industry and academia, a number of TUX-related efforts are in play. For example, in 2007 we assembled a TUX Advisory Board of passionate experts from across the company to help product teams with their critical TUX and to hone and validate best practices. On the education front, some schools now offer study in this field (e.g. Carnegie Mellon University has a Center for Usable Privacy and Security).
Join the discussion
As we and others investigate and mature this discipline, it’s important to leverage the great work that has already been done and to find ways to collaborate. The End to End trust discussion is one such forum for engaging in that dialog.
Our ability to make good trust decisions starts with a trustworthy system. Per the End to End trust vision, we need to build in trust from the bottom up (i.e. a trusted stack) -- and it will take a global village to harden critical infrastructure components like the Internet. Identifying and deploying common metaphors for establishing trust relationships and making trust decisions will help reduce the learning curve for users and enhance the overall safety of consumers and enterprises.
What good is building great trust plumbing if we end up making silly mistakes in the last two feet?
Jeffrey Friedberg
Chief Trust Architect
Microsoft Corporation