22A/ The Verifiable Credentials Functional Stack
The Verifiable Credential Stack
Thursday 22A
Convener: Timothy Ruff
Notes-taker(s): Neil Thomson
Tags for the session - technology discussed/ideas considered:
VCs/Verifiable Credentials, SSI, ToIP, Business of SSI
Discussion notes, key understandings, outstanding questions, observations, and, if appropriate to this discussion: action items, next steps:
Story
1956 Malcom McLean – inventor of the shipping container – contributed more to world trade than any other changes in 50 previous years.
Cost of $5/ton -> 16 cents. Took 10 years due to resistance to change
Verifiable Credentials is the shipping container of Authentication.
There is disagreement about a lot of the ways forward (block chain vs. KERI)
What is being getting a huge support for is verifiable credentials
LER – learning and employment record – for Universities – as a standard on course accreditation via verifiable credentials
What are the contents of a credential to verify, but the concept is a done deal
How data moves today is similar to pre-container shipping. Add verifiable credentials to the data and it becomes containerized
Prove to a lender I still have a job. The only way to do is via equavac or call previous
employers. With verifiable credentials, that problem goes away.
Looking at SSI, possible places for verifiable credential storage – (all currently in play)
• Blockchain vs. KERI vs. Wallet vs. database
Individual is courier about own stuff. They can make a claim, which an employer can validate and hand that back to the user (to store in “wallet”).
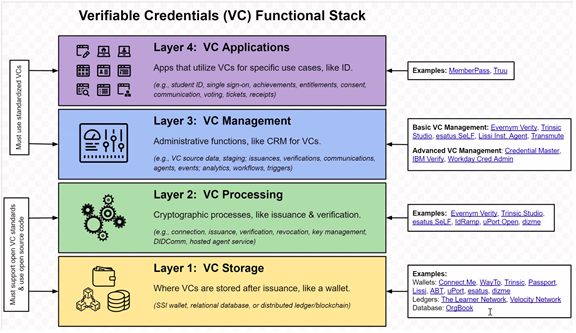
The following (unlike the TOIP stack) is a VC container centric stack
There is a blog on this
Where does VC from layer 2 go – BC, DB or Wallet
Layer 3 – we are going to be awash in VCs. With performance improvements in VC processing, this will explode with thousands per person (which can be very short time frame) and millions per organization. This provides traceability of verified transactions.
What if a university id generates many VCs for all access on campus.
Verifiers can now track when a user has accessed their services
Layer 4 is where it touches users – new payment systems, voting systems, etc. all VC driven. Example – enable student to take selfy for ID purposes that becomes a VC
Managmeent of VCs MAY be simple (currently are not) and can be distributed (as well partitioned) and specialized.
What are the points for “bespoke” code vs. off-the shelf – V4 is likelyto be the most customized, lower layers more standardized (as you go down).Interoperability from 3 down is required.
Force big tech to hand stuff back to people so they can port their VCs and “stuf” to other vendors (VCs as portable model)
To be competitive at layer 4, those VCs must be portable (vs. lock in)
Connections – in layer 2, but connection management will be critical
Killer use of SSI is point to point connections to support CRM communication.
Can’t verify a credential without the connection.
Connections are created as required, but connection management (about what connections can be contructed and are validated) are critical
Idea: Credential Connection – e.g. service account at electrical supplier – supplier provides credential validated connection to the connection, which allows user to delegate use of that account to someone else.
Example of performance improvements
• KERI – issuance, verifiation
• BBS+ builds on zero knowledge proofs, which are scaleable milliseconds vs. seconds
• <undisclosed developer> revocation (formerly difficult) now simple/fast
Any area is open to disruption is when there is a data imbalance (e.g. simplification and lower transaction time/cost is a killer)
Lacking discussion in SSI space – how are you going to make mone?
Actually Tinsic sessions on SSI stat of the business are AT IIW31 (Riley Hughes chicken and egg)
Where am I going to build vs. buy.
Anticipated – wallets built into phones (alternative – cloud wallets provided with services, etc.)
Verifiable COVID-19 credentials – is a Layer 2 problem, user has to carry around the credential in a wallet and/or app?
Airlines have to verify and track all the user/s credentials – layer 3
Layer 4 – is where you have to hide all the complexity – they should NOT have to deal with the NASCAR problem.
QR interface is Layer 4
Trust Triangle for agrigulture – and how farmers fit. Farmers don’t control their data and are not at the table in discussing (so far). Farmers want it and are willing to invest. No one wants to be the first to put the baby in the car seat in the autonoumous car. So building the entire stack is a challenge as it does not exist (yet).
Can you transfer a VC. You can’t as a VC is only issued to a unique Identity (person).
While a vehicle has an independent ID, which can have VCs which are tranferable from one person to another.
A ticket is tyipcally issued only to a specific identity (say as VC), which the ticket issuer can make transferable or locked – would be an aspect of the ticket’s credential.
Identities vs. credential vs. connection – the distinction is fuzzy
Farmer use case discussion
Supply chain includes supliers distributers and processors
Farmer has to put data into the system (including personal information and economic records), with no control (vs. VC). Yet grocers have to provide traceability to the farmer for various reasons.
There are use cases.
The easy part of the problem is to envision the future state (end game and the benefits). The hard part is where to start and how to fund it. Farmer level is cooperative non-profit. Figuring out who plays what role.
Before you get to the stack – Running Lean – by Ash Maria – for taking an idea and turning into profits. Problem/Solution fit (before Problem/Market fit) and how are you going to (initiallyl) make money.
The money maker is ideally a tiny slice that pays big (saves costs or makes money for customer)
Value proposition that the client will pay for.
Has a processor that would pay for it (need to refine)
Use the “Lean Canvas”
Verifiable credentils with multiple presentations (e.g. VC contains multiple claims). Or would university issue multiple VCs per student.
No currently facility to update an existing VC once issued. Currently will have multiple credentials.
Potential for VC “set” which is a collection of related VCs.
Frustrating that the SSI adoption rate is slow.
T. Ruff has been talking about VCs for 4 years
Need to understand: VCs and Data Access/Transfer
What is new – the user owns their data and directly controls connections and use
Porting VC to IoT – in context of passive and active identifiers/crentials (was a session during this IIW
All the ingredients are there to day to secure IOT
In talking with a mortgage processor – the ability to have a persistent conection to the borrower and lender. Many potential VCs involved in a mortage broker scenario.
Could reduce mortgage processing from 1+ month to 2 weeks.
Another use case – VCs for criminal record checks for non-profits (primarily a cost at the police level in Canada).
GOOTB – get out of the building and talk to an actual customer. Threshold is a minimum of 20 customer conversations, then validate with another 20 more. THEN you can talk with the money.
Best way to fund is with revenue – pre-orders from customer is very credible
Back to MVP – minimal viable product
Credential Master – volume credential manager at layer 3, based on sales force
Chat:
From RuffTimo : brb
From John Court : Most here in OZ just insist on seeing some recent payslips !
From Debbie Bucci : actually the ask customer to physically produce w2 for 4 weeks ... so the verifiable claim seems to align - if my employer would be able to release ...
From Debbie Bucci : yep
From Dan Robertson (he/him) : And with ZK proofs, that process can preserve privacy much better than the "here are my W2s" model we have now...
From Ashok Dhakar : When you relational database, will it allow to use NoSQL databases as well?
From John Court : Layer 1 - Physical, Layer 2 - Communications, Layer 3 - Session/Management, Layer 4 Application …..hmmm seems to follow a well known pattern
From Karen Hand : Does anyone have a ballpark idea on cost and time to implement a MVP for a simple trust triangle?
From Debbie Bucci : Revocation has alway been an issue ...
From Gabe Cohen : ZK revocations, yes
From Neil Thomson : https://medium.com/@rufftimo/verifiable-credentials-arent-credentials-they-re-containers-fab5b3ae5c0 Timo Ruff credential blog
From Neil Thomson : Riley Hughes (Trinsic) has done two sessions on SSI business Chicken and Egg @ this IIW - recorded
From John Court : I guess that makes it a Bearer VC
From Neil Thomson : Running Lean book https://www.oreilly.com/library/view/running-lean-2nd/9781449321529/
From Will Groah : Always enlightening to hear your perspective, Timothy. We are currently working a the business model aspect of converging VCs with background checks, particularly if cases where the user is paying for the background check. Interested on your quick perspective and/or perhaps offline discussion.
From Vic Cooper : https://www.albertosavoia.com/therightit.html
From Neil Thomson : Technololgy is complicated. You need to get to the point where "you can ignore the man behind the curtain"
From RuffTimo : Thanks Will!
From Karen Hand : For us, we have the relationships and reputation which is putting us in the boardrooms. Has been very important.
From Mawaki : Vic, your link doesn't seem to work.