"Entity and Object Identifiers: Bringing assurance and immutability to a decentralized network"
Entity & Object Identifiers: Bringing Assurance & Immutability to a Decentralized Network
Tuesday 4I
Convener: Paul Knowles (The Human Colossus Foundation)
Notes-taker(s): Paul Knowles
Tags for the session - technology discussed/ideas considered:
Discussion notes, key understandings, outstanding questions, observations, and, if appropriate to this discussion: action items, next steps:
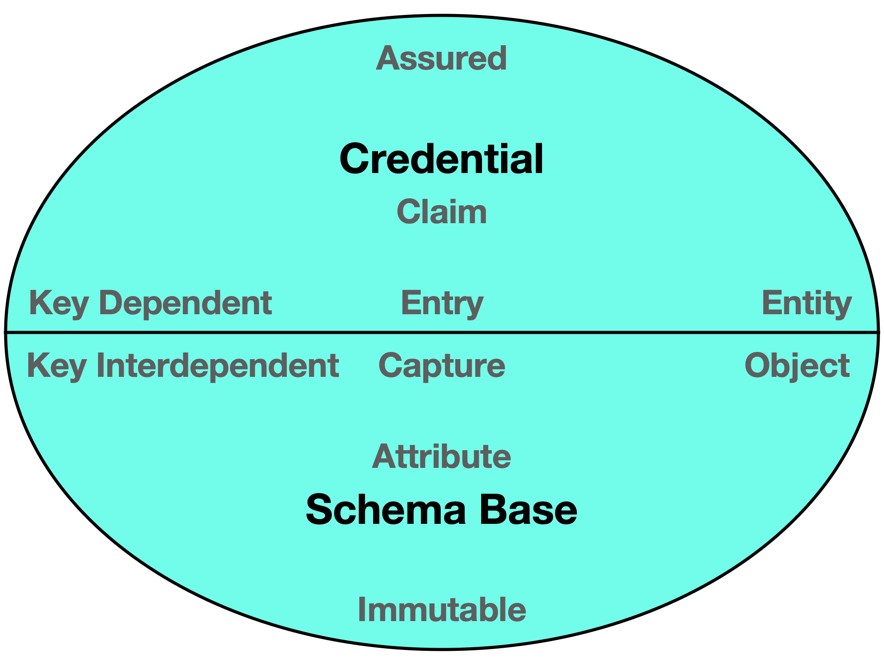
A digital network must contain assured data entry and immutable data capture elements in order to maintain integrity. Data entry can be referred to as the “male” (or yang-) side of a decentralized network model due to the requirement of a signing key in order to establish that inputted data has come from an assured source. Conversely, data capture can be referred to as the “female” (or yin-) side of the model due to the provision of immutable fields in order to capture and store inputted data. The following component model indicates the yin-yang synergy of a balanced network with everything in the northern hemisphere representing the male side of the model and everything south of the equator representing the female side.
Figure 1. A component diagram showing male and female counterparts in a balanced network model.
In figure 1, elements, components and characteristics in the top half of the model fall into the “Credential” space, the data entry domain, while those in the bottom half fall into the “Schema” space, the data capture domain.
The characteristics of the identifier types required for data entry and data capture differ. In the case of data entry, assured entry elements are identified by entity identifiers, a type of identifier that is governed by an entity who controls the signing key. In the case of data capture, on the other hand, immutable capture elements are identified by object identifiers, a type of identifier that contains a hash of the content of an object. The following hash grid table describes the different identifier states.
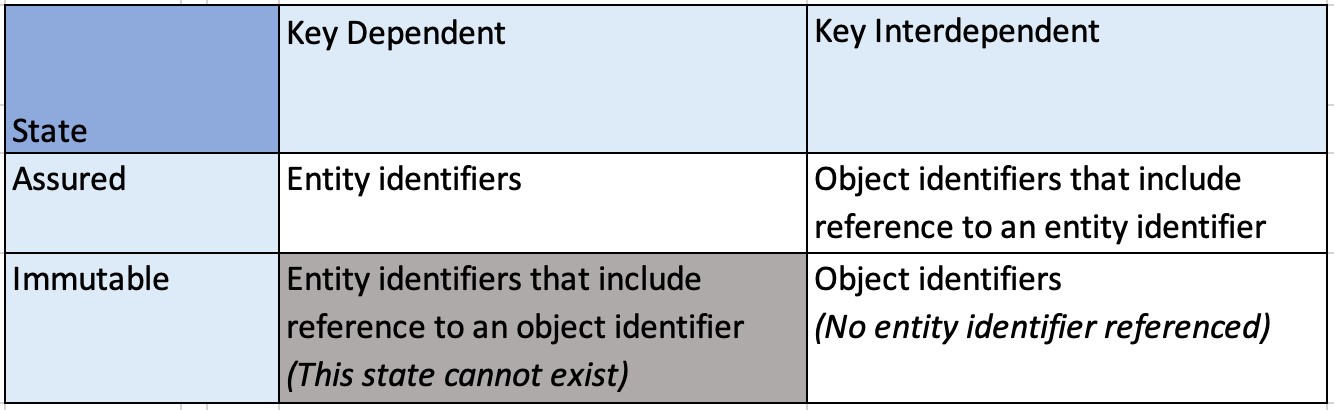 Figure 2. A hash grid table describing the different states of entity and object identifiers.
Figure 2. A hash grid table describing the different states of entity and object identifiers.
To help dissect the characteristics of the identifier hash grid table described in figure 2, the meanings of the associated characteristics need to be defined.
Key Dependent vs Key Interdependent
Key Dependent:
The identifier is governed by an entity and therefore a signing key is required.
Key Interdependent:
The identifier can either be governed by an entity (whereby a signing key is required) or not governed (no keys required).
Assured vs Immutable
Assured: The identifier is governed by an entity and therefore a signing key is required to establish assurance.
Immutable: The identifier contains a hash of the content of an object which cannot be changed. If an object identifier is governed, the controller of the signing key has control over the content contained within an associated identity document and, as such, it can no longer be deemed immutable.
To scale this back to the Credential and Schema domains in the network component diagram shown in figure 1, this essentially means that all elements within the male side of the model should be signed by a signature key as proof of governance to establish assurance. All elements within the female side of the model, on the other hand, should contain a hash of content to establish immutability.
As a summary statement, entity identifiers bring assurance and object identifiers bring immutability to a decentralized network.
Note: The Human Colossus Foundation will be introducing key components of a Decentralized Data Economy (DDE) through a series of blog posts over the course of 2020.